Secure deploy and manage all users apps and devices without. What Is Endpoint Detection and Response and How Does It Work.
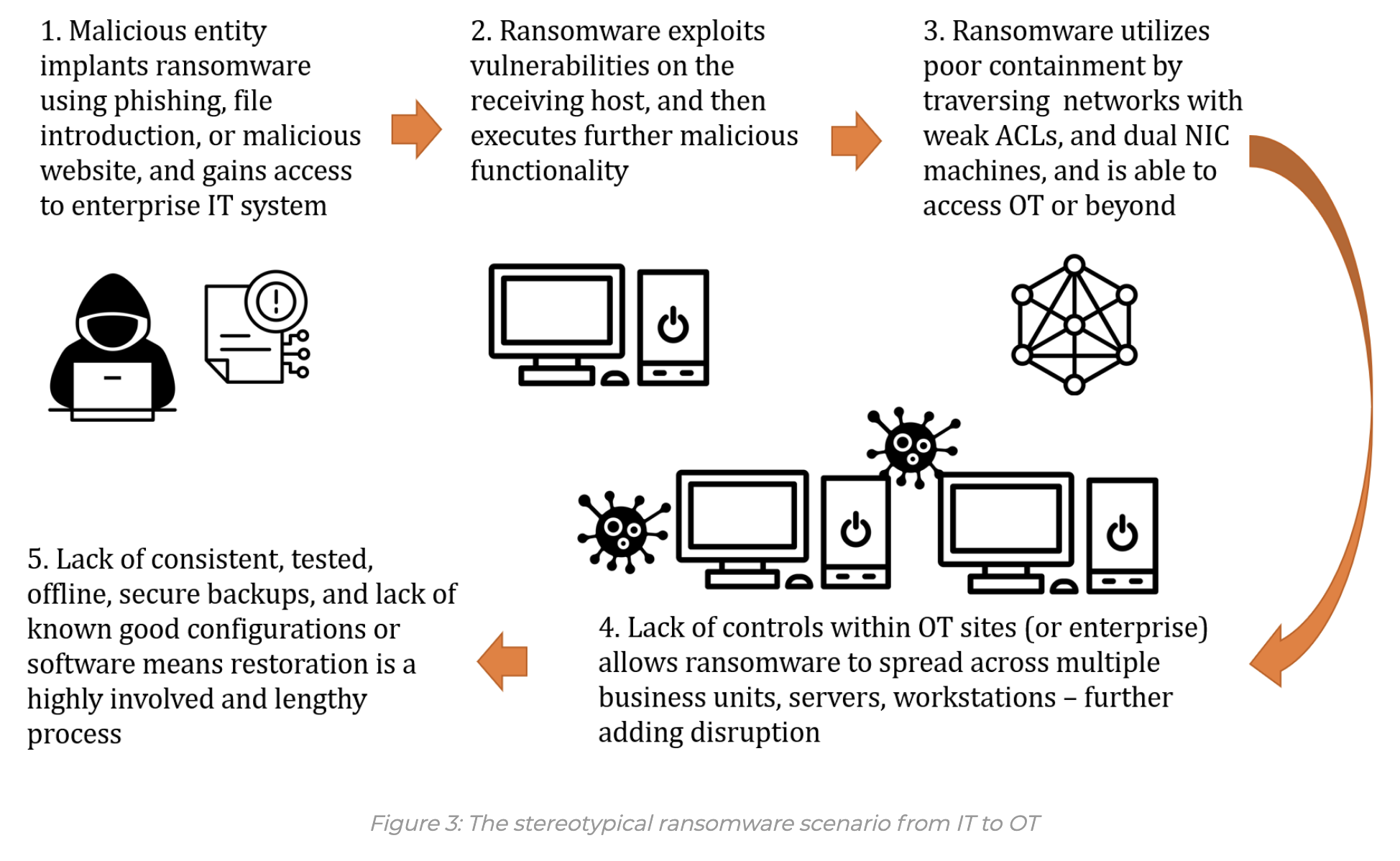
How To Prevent Ransomware In 2022 Verve Industrial
Rev J - Combating Ransomware.
. Use application sandboxing and code analysis as well as app-security. EDR solutions typically aggregate data on endpoints including process execution endpoint communication and user logins. Ryuk is one of the first ransomware families to include the ability to identify and encrypt network drives and resources as well as delete shadow copies on the endpoint.
1M healthcare records. Analyse data to discover anomalies and malicious activity. Removing Clop Ransomware from Windows 7Vista Windows 881 Windows 10 Windows XP.
How do I create an Access Protection rule for a file or folder in systems. Threats on the Rise. Why do I need an enterprise antivirus solution like Endpoint Protection.
How Can You Remove Clop Ransomware. User-defined Access protection rules prevent changes to files or. Endpoint Protection provides centralized protection for all of your Windows Mac and Linux workstations including laptops smartphones and the leading virtualization systems.
Learn the best defenses against ransomware including how to protect your devices and how to fight an infection. Ransomware attacks cause downtime data loss possible intellectual property theft and in certain industries an attack is considered a data breach. Endpoint Protection.
51 increase o Increased throughout year o Peaked SeptemberOctober at 87 increase Emsisoft Ransomware statistics for 2020 o 560 healthcare organizations impacted Wall Street Journal HHS. An endpoint can be an employee workstation or laptop a server a cloud system a mobile or IoT device. Ransomware infiltrates your device.
And record data about malicious activity enabling security teams to investigate and. WannaCry is an example of crypto ransomware a type of malicious software malware used by cybercriminals to extort money. While other types operate undetected ransomware makes its presence known immediately demanding payment in exchange for returning access to your device or files.
Carbon Black EDR continuously records and stores endpoint activity data so security professionals can hunt threats in real time and visualize the complete attack kill chain. Prevent zero-day and ransomware attacks. Ransomware is defined as vicious malware that locks users out of their devices or blocks access to files until a sum of money or ransom is paid.
When the device is again connected to the network and the remote file is. Begin with running your system in a Safe Mode. Endpoint Manager meets organizations where they are in their cloud journey.
Why do I need Anti-Ransomware. How to Mitigate an Active Ransomware Infection. Below you can find the instructions to detach Clop ransomware from Mac and Windows computers.
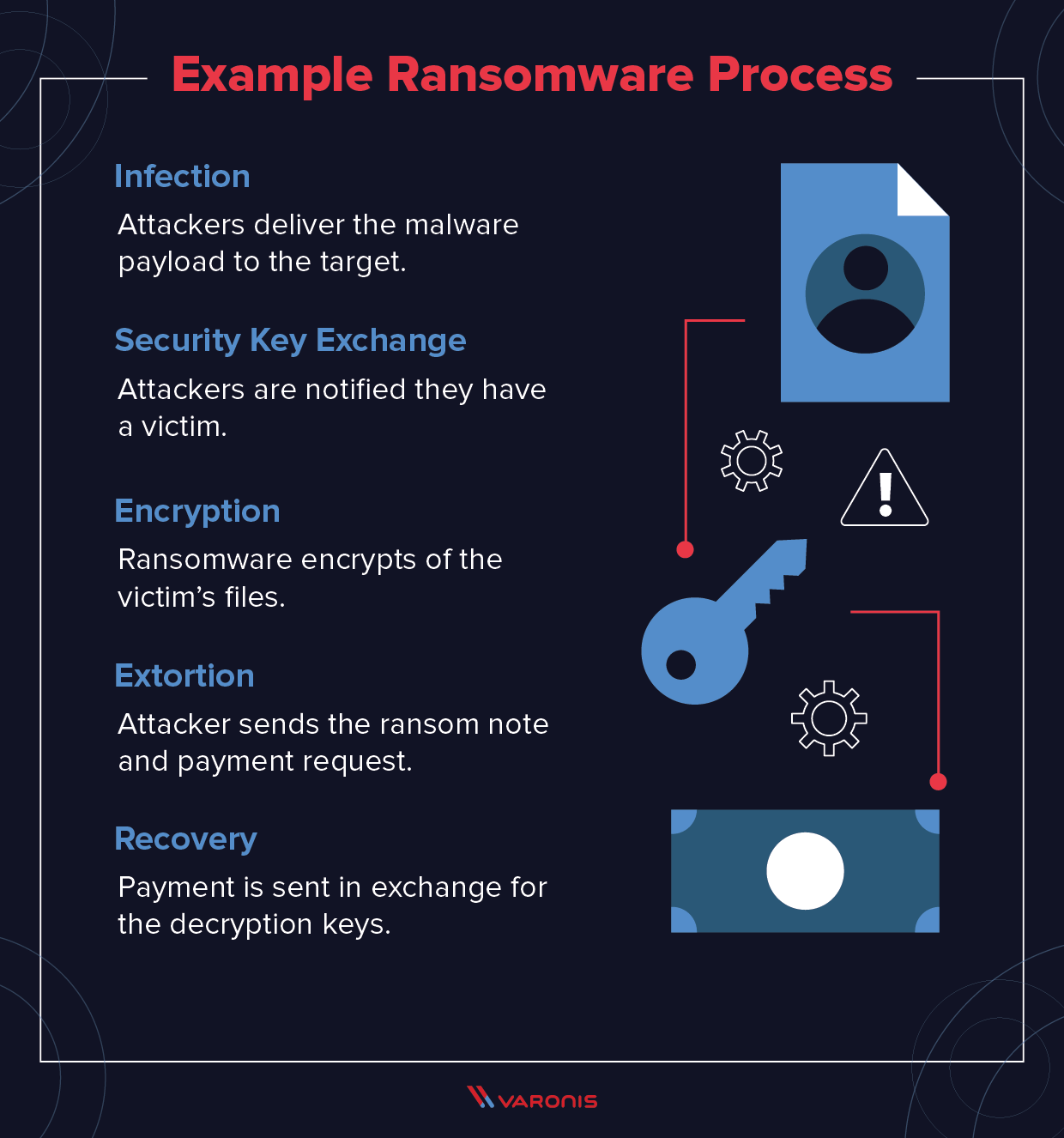
By pbust January 27 2016. Ransomware that uses encryption is called crypto ransomware. September 2013 is when ransomware went pro.
It lived up to its name by infecting hundreds of thousands of computers in over 150 countries in just a few hours. CylancePROTECT is an AI-based Endpoint Protection Platform EPP that stops cyberattacks and breaches. Many successful ransomware attacks are only detected after data encryption is complete and a ransom note has been displayed on the infected computers screen.
In most cases malware is much harder to observe toiling quietly behind the scenes. Digital Literacy in 2022. At this point the encrypted files are likely unrecoverable but some steps should be taken immediately.
This means the attackers can then disable Windows System Restore for users making it impossible to recover from an attack without external backups or rollback technology. Stop memory-based attacks and exploitations. On the other hand WannaCry was more of a catapult.
Ransomware is the most confrontational and direct form of malware. Average of 816 attempted attacks per healthcare endpoint o 9851 increase from 2019 o Between January and February. Manage USB device usage and prevent unauthorized devices.
Keep any computer or device that connects to your company virus free. Ransomware does this by either encrypting valuable files so you are unable to read them or by locking you out of your computer so you are not able to use it. Put employees first with device choice.
Does the Endpoint Migration Assistant migrate rules that are assigned. What does malware do. Get endpoint security device management and intelligent cloud actions in a unified management platform with Microsoft Intune and Configuration Manager.
We have placed cookies on your device to. To plant the DarkSide ransomware the gang apparently took advantage of a known password for a legacy Virtual Private Network VPN account.

Fortinet Ransomware And Phishing Prevention Solutions
Best Practice Configuration Against Ransomware Endpoint Application Control

Prevent Cybersecurity Breaches Comodo Cybersecurity Security Solutions Intrusion Prevention System Device Management
0 Comments